AVW200 and Secure by Default: What You Need to Know
par Eric Schmidt | Mis à jour le : 08/28/2025 | Commentaires : 0

Cybersecurity isn’t just a buzzword. It’s an everyday priority. In today’s world, where data privacy is critical, keeping your monitoring systems secure is just as important as keeping them accurate. That’s why we at Campbell Scientific introduced Secure by Default—an initiative designed to strengthen data logger security across our entire product line.
Sometimes big improvements come with unintended consequences. One of those surprises is how Secure by Default affects certain peripheral devices—such as the AVW200 2-Channel Vibrating Wire Analyzer Module and the CCFC Outdoor Observation and Surveillance Field Camera—when you’re connecting them to a newer data logger on a PakBus® network.
Why This Happens
A key feature of Secure by Default is that PakBus encryption is automatically enabled. This means all communications between PakBus devices are protected; messages are encrypted on one end and decrypted on the other.
The challenge? Some older devices (including the AVW200, CCFC, and older PakBus products) don’t support PakBus encryption. So, when you connect them to a CR6 Automated Monitoring Platform or CR1000Xe Measurement and Control Datalogger, they can’t understand the encrypted messages or send encrypted messages back. To you, it looks as if the device just isn’t working.
How to Get Your AVW200 Working Again
Fortunately, you’ve got two options to bring your system back online:
- Turn off the encryption for the data logger.
- Using LoggerNet Datalogger Support Software and the Device Configuration Utility, connect to your data logger and disable encryption.
- This is quick and effective, but keep in mind it makes your network less secure.
- Use the EncryptExempt() instruction in the CRBasic program.
- Add the EncryptExempt() instruction to your program to “exempt” your AVW200 (or other older device) by its PakBus address.
- This keeps encryption active for every other device on your network, maintaining a higher level of security.
Here’s what that looks like in CRBasic:
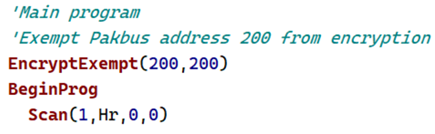
Place the instruction before the “BeginProg” and “Scan” lines in your CRBasic program. You can also set a range of addresses. For example, “EncryptExempt(200,202)” would exempt PakBus addresses 200, 201, and 202.
Final Thoughts
Secure by Default makes your network stronger, but it can take a little adjustment when working with certain devices. By using the EncryptExempt() instruction, you can keep your system secure without sacrificing functionality.
At the end of the day, our goal is simple: we want to give you the tools to collect reliable data confidently and securely.
Need help?
If you’ve tried the steps above and your device still isn’t working, we’re here to help. You can reach out to our Support Team at support@campbellsci.com or contact me directly at eschmidt@campbellsci.com.



 Eric Schmidt is an Application Engineer in the Infrastructure Group at Campbell Scientific, Inc. He works with customers on the technical aspect of building measurement systems; helps provide trainings for all of Campbell Scientific’s international offices; and attends conferences related to dams, mines, and geotechnology. He received his bachelor’s degree in biological engineering from Utah State University. In his spare time, he enjoys canyoneering and composing music.
Eric Schmidt is an Application Engineer in the Infrastructure Group at Campbell Scientific, Inc. He works with customers on the technical aspect of building measurement systems; helps provide trainings for all of Campbell Scientific’s international offices; and attends conferences related to dams, mines, and geotechnology. He received his bachelor’s degree in biological engineering from Utah State University. In his spare time, he enjoys canyoneering and composing music.
Commentaires
Please log in or register to comment.